Introduction
I just finished the 2025 Snyk Fetch the Flag event, co-hosted by Snyk and John Hammond. This 24-hour Capture the Flag (CTF) competition marks my second experience in this format. Despite some initial infrastructure challenges, the overall event was highly positive, featuring well-designed and engaging challenges. The organizers effectively balanced the difficulty of the challenges, while providing a rewarding experience for both novice and expert participants. The challenges spanned various cybersecurity domains, including web exploitation, binary exploitation, reverse engineering, cryptography, and forensics, with multiple tiers of difficulty within each category.
I completed a new personal record, completing 8 challenges which contributed 798 of our team’s total of 998 points. I successfully completed challenges in the web exploitation, forensics, cryptography, and reverse engineering categories. Given my extensive background in leading web development teams, the web domain might seem like a natural area of expertise. However, my prior CTF experiences have yielded limited success in this category. My recent participation in CactusCon’s “Greenhouse” village, which focused on hands-on learning, significantly improved my proficiency with Burp Suite, particularly some of the more advanced uses of the Interceptor and Intruder functionalities. This new knowledge helped me multiple times during the Snyk Fetch the Flag event to come up with attack vectors, prove hypotheses, and give insights into the functions of many of the challenges.
In addition to solving the challenges, I committed to documenting my process through detailed write-ups, which are available on my GitHub. This document will focus on one of the more complex web challenges, “WHO IS JH,” where I felt I significantly expanded my technical capabilities.
WHO IS JH
The “WHO IS JH” challenge, and many others, provided us with the site’s source code and a Docker file for local deployment, a feature I found particularly beneficial. This allowed for iterative testing and refinement of attack strategies in a controlled environment before deploying against the hosted instance. While minor discrepancies existed between the local and hosted environments, the overall experience was seamless.
The premise of the “WHO IS JH” site revolved around the “multi-John-Hammond” conspiracy theory, suggesting that John Hammond is a time-traveling individual making significant contributions across various fields of music, dinosaur theme parks, and cyber security. The challenge focused on exploiting vulnerabilities within the “Upload Evidence” and “The Conspiracy” pages.
Analyzing the “Upload Evidence” page’s code we can see that the code enforces a file extension check, accepting only .png, .jpg, or .gif files. However, this method does not guarantee the actual file type, as we will see. After passing the extension check, a unique identifier is prepended to the filename, and the file is saved in the “uploads” directory, with a corresponding log entry that is written to a file on the server.
$uploadDir = 'uploads/';
$allowedExtensions = ['jpg', 'png', 'gif'];
if ($_SERVER['REQUEST_METHOD'] === 'POST' && isset($_FILES['image'])) {
$originalName = basename($_FILES['image']['name']);
$fileTmpPath = $_FILES['image']['tmp_name'];
$fileExtension = strtolower(pathinfo($originalName, PATHINFO_EXTENSION));
$uniqueName = uniqid() . "_$originalName";
$uploadPath = $uploadDir . $uniqueName;
if (in_array($fileExtension, $allowedExtensions)) {
if (move_uploaded_file($fileTmpPath, $uploadPath)) {
logEvent("Uploaded file: $uniqueName");
$message = "Your file <strong>$originalName</strong> has been uploaded successfully! The truth is out there.";
} else {
logEvent("Error moving file: $originalName");
$message = "Something went wrong during the upload. Is someone tampering with the evidence?";
}
} else {
logEvent("Invalid file type attempted: $originalName");
$message = "The file type you uploaded is not allowed. Are you trying to sabotage the investigation?";
}
} else {
$message = "No file uploaded. Do you have evidence, or are you just here to observe?";
}
Reading the Logs
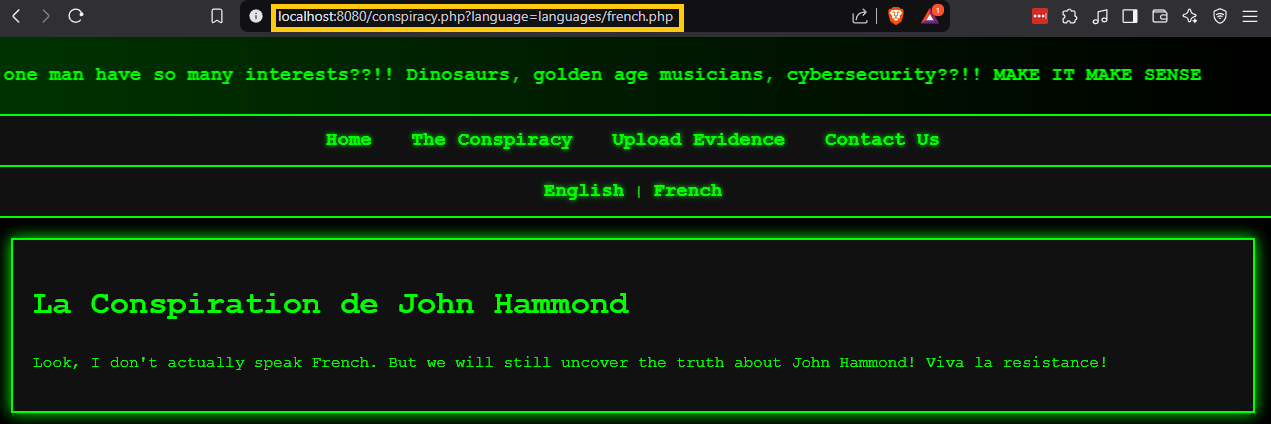
The “Conspiracy” page featured a language selection option. Switching to French modified the URL, introducing a query parameter that resembled a file path and rendered a PHP file.
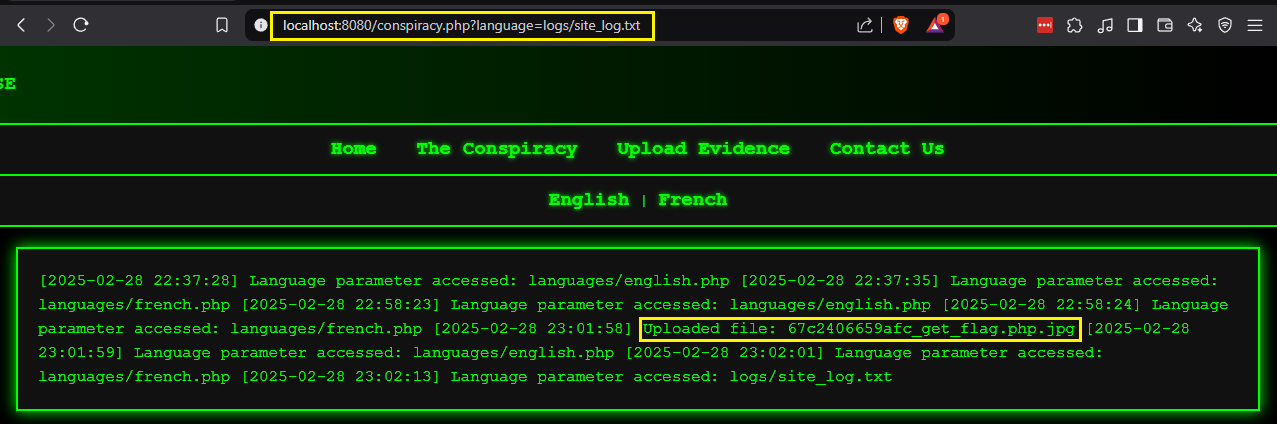
Inspecting the Docker container showed the log file’s location at logs/site_log.txt. By substituting the language file path with the log file path in the URL, we successfully accessed the server logs, revealing the renamed uploaded file.
Crafting the Payload
Having identified a method to execute arbitrary code, we proceeded to craft our payload. The file extension check could be bypassed by including a PHP extension (.php) then appending a legitimate image extension (.jpg). This allowed us to upload a file named get_flag.php.jpg containing PHP code. The query parameter on “The Conspiracy” page could then be used to execute this file as PHP.
Inspecting the Docker file we could see that the flag’s location was in the root directory at /flag.txt further inspection of the Docker configuration file showed that some system functions were disabled (exec, system, shell, passthru, etc). However, the readfile() PHP function remained available. Using that knowledge I used this code in the malicious file.
<?php echo readfile('/flag.txt'); ?>
Retrieving the Flag
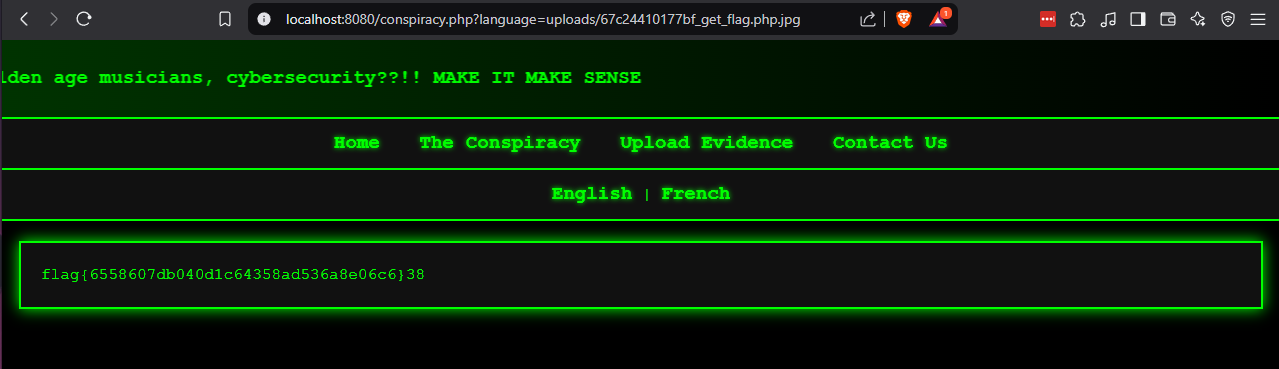
By modifying the query parameter on the French “Conspiracy” page to uploads/[random_id]_get_flag.php.jpg, we successfully executed our uploaded file and retrieved the flag.
Conclusion
This challenge demonstrated the complexity and depth of the Snyk Fetch the Flag challenges. They required a nuanced understanding of system interactions rather than a simple tool-based approach. This mirrors real-world security scenarios, where vulnerabilities often arise from the interplay of multiple systems.
As developers and security professionals, we must adopt an adversarial mindset. Recognizing that file extensions are mere indicators, not guarantees, is crucial for building robust upload mechanisms. Similarly, understanding the potential for query parameter manipulation is essential for preventing unauthorized file access and execution. Attackers only need to exploit a single entry point, and the complexity of modern systems necessitates a comprehensive approach to security.
While developer and QA education is vital, dedicated security teams provide specialized expertise in threat modeling and vulnerability assessment. This diversity of skills and perspectives strengthens our ability to protect our critical systems and data. Participating in events like Snyk Fetch the Flag help me to fully grasp the importance of continuous learning and professional development in technical roles. And while I don’t think I will ever work as an analyst in a SOC or be a member or a Red Team, understanding the basics of the tools they use and how some exploits are performed make me a better leader and help me design and deliver robust and security minded products.
